Hacking another person’s phone isn’t as complex as you’d imagine. Rapid advances in technology have made it easier for hackers to infiltrate corporate systems, personal computers and even smartphones. According to statistics, about 800,000 people fall victim to cyberattacks every year. However, there are numerous measures you can take to prevent any phone hacker from accessing your device.
If you’re trying to protect your child from online scammers, checking their phone activity frequently can help you identify any potential red flags. Fortunately, you can hack a cellular phone using a variety of methods – all of which are discussed in this article.
Hacking a Phone: Legal and Ethical Boundaries
Mobile security is a vast field that should be handled with sobriety and caution. Hacking another person’s phone is considered to be a criminal offense in most countries. In addition, it’s a serious breach of privacy that carries stern legal repercussions. It’s, therefore, important to seek legal counsel before hacking anyone’s device.
It’s also unethical to check a person’s phone without their consent, particularly if they’re not your partner or child. People with strong moral standards are required to maintain their ethical standpoints and look before they leap. If your curiosity prompts you to hack someone’s device, then your moral fabric could be significantly corroded.
There are few instances where monitoring other people’s phones is considered legally and ethically right. For instance, if the individual being tracked is a minor or they consented to being monitored, then you can check their phone with a clear conscience. The target device could also belong to you, in which case you’re allowed to track it.
6 Best Ways to Hack Someone’s Smartphone
Hacking a phone doesn’t have to be a sophisticated affair. In fact, you can access someone else’s emails, SMS texts and social media chats using a variety of methods. Here are some of the best ways to hack another person’s smartphone:
Method 1 – How to Hack an Android Phone by Sending SMS
How to get into someone’s phone remotely? This black-hat technique involves sending spam texts to your target user in an attempt to fool them and gain access to their Google account. Most people who use Android phones usually link their Google accounts to social media, their bank accounts, eCommerce shopping sites and more. If you manage to hack into your loved one’s Gmail account, you’ll have access to tons of confidential info.
In order to log into their Google account, you’ll need their password. Alternatively, you can spam the target device with messages in order to obtain a security code that you’ll use to sign in. Here’s a step-by-step process that explains what you need to do:
- Visit the Google sign-in page. Enter the target phone’s mobile number and click “Forgot Password.”
- A verification code will automatically be sent to that device.
- If you can’t access your loved one’s phone physically, send them a spam text message.
- This message can appear as follows: “Google has noticed an unauthorized activity on your account. To fix the issue, reply with the Google verification code that was sent to your number.”
- Once the spam text has been sent, wait patiently for the reply. If they send you the code, then you’ve successfully fooled them.
- Use the verification code to create a new account password and log into their Google account.
- Track their activity in real-time and view all the data you need.
Apart from viewing their emails and messenger chats, you can also discover their favorite shopping malls and track their live location. Sadly, modern phones are well protected with strong encryption systems, making it difficult to hack them using this method.
Method 2 – Phonsee
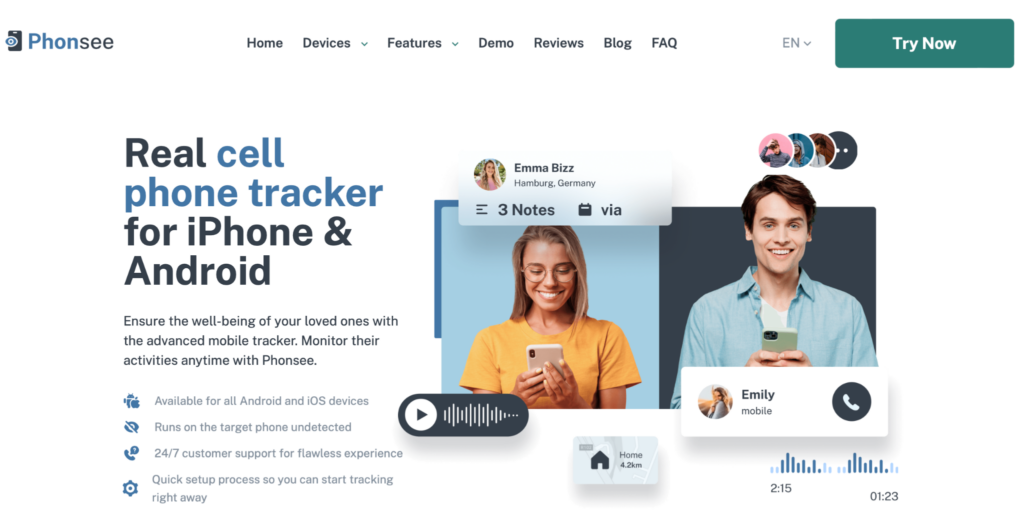
A better solution you can use to monitor someone else’s phone is Phonsee. You can use this particular app to tap into someone’s phone remotely and obtain their call logs, SMS text, social media chats, email conversations and more.
Phonsee’s most popular tracking features include:
- Social media monitoring. This feature allows users to view every incoming and outgoing message on Facebook, WhatsApp, Instagram, Kik, Viber, Tinder, Telegram and an assortment of similar messenger apps.
- GPS location tracker. You can view your target’s real-time location on a map. In addition, you can check their route history and create virtual boundaries so as to get alerted every time they cross those geofences.
- Keylogger and screenshot capturing. Wondering who they’re chatting with on social media? Phonsee takes regular screenshots and stores them in your Control Panel for later viewing. It also records everything they type using an accurate keylogger.
- App & website blocker. If they’re browsing inappropriate websites or using apps you don’t approve, Phonsee allows you to block these suspicious sites with the click of a button.
- Call history monitoring. You can conveniently monitor their call logs and check their contacts to discover who they interact with the most.
- Text message scanner. Read through their secret SMS messages, complete with recipient details and timestamps, using this superb app.
How to install Phonsee
Follow these simple guidelines to install Phonsee on the target device:
- Visit https://phonsee.com/ on your PC browser.
- Sign up for a free account using your email address and password.
- Choose your preferred subscription and complete the payment.
- Check your mailbox for detailed instructions sent by Phonsee.
- Follow the provided guide to install and configure Phonsee.
- Log into your account and track your target’s cell phone remotely.
Method 3 – Phishing Attacks
Phishing simply entails using technology to obtain other people’s private information illegally. One popular phishing technique involves luring unsuspecting users into providing their account credentials using fake versions of popular websites such as Instagram or Gmail.
In case you’re tech-savvy enough to create a mock-up site and subsequently acquire your target user’s login credentials, you’ll easily infiltrate their phone with little hassle.
Unfortunately, this method is illegal. You also ought to have a technical background in order to design a fake site.
Method 4 – Control Message
Learning how to hack someone’s phone can even help you unearth whether your spouse is cheating. Consider using control message attacks to access the target device’s “Settings” menu and compromise its security protocols.
Once a control message is sent to a given device, it provides unrestricted access to that phone’s settings. You can uncheck SSL, remove all safety features and send all backup data to your phone before executing a wipe command.
However, modern smartphones come with intricate encryption systems that are unsusceptible to such attacks. Your target user can also discover they’re being attacked and contact the police.
Method 5 – Midnight Raid
Another tactic you can utilize to hack a cellular phone involves executing a midnight raid. This attack often occurs at night when the target is sleeping, hence its title. To succeed, you’ll need a PC, a strong internet link and two phones (one operates as a GSM modem while the other receives data).
To start, a simple message is sent to the target device stating “You’re being hacked.” once the message is received, Internet Explorer immediately pops up, and then a data-retrieving malware is run. The target device returns the SMS back to the original phone, carrying along its IMSI code.
This solution can be used to steal any type of data from a device. However, it’s highly unethical and can lead to the loss of confidential information. You also risk infecting both phones with malware.
Method 6 – Data Extraction Through a USB Charger
You can also learn how to hack somebody’s phone using a USB lightning charger. However, you’ll need physical access to the target device for this solution to work.
First, open your PC and connect your loved one’s phone using a USB charger. Once the device is detected and all the necessary drivers are installed, open its folders and copy all the information you need to your computer.
Despite being a remarkably simple process, you ought to know the target user’s phone unlock passcode and keep their device for a lengthy period.
How to Know if You Have a Tracking App Installed on Your Phone?
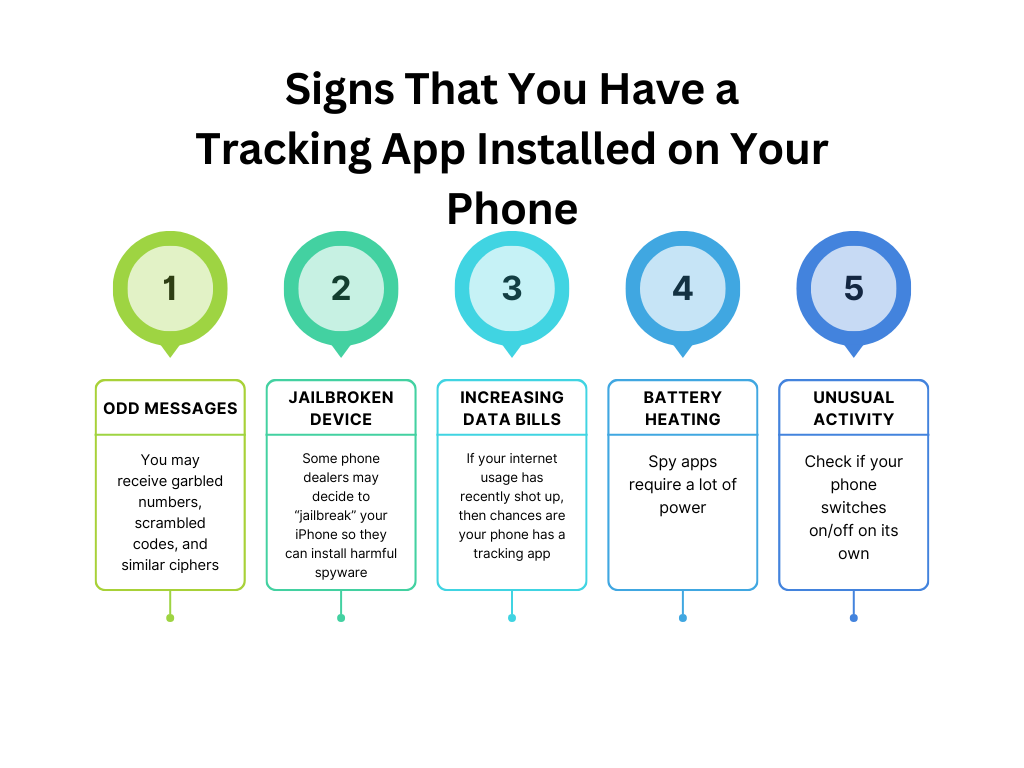
Here are some tell-tale signs that indicate someone has installed a tracking app on your phone:
Hackers may send garbled digits, confusing codes and similar ciphers to your phone in an attempt to “instruct” spyware to send your confidential data.
Some phone dealers may decide to “jailbreak” your iPhone so they can install harmful spyware and track your every move. It’s difficult to differentiate an original phone from one that has been altered. However, you could stumble upon the software that was used to perform this action.
If your internet usage has recently shot up, then chances are your phone has a tracking app. Such apps utilize GPS for live location monitoring as well as data roaming to send information, causing your Wi-Fi utilization to go through the roof.
Other signs include your phone regularly shutting down/restarting and your device battery becoming unbearably hot.
Conclusion
Evidently, hacking a phone doesn’t require any specialized expertise. You can conveniently track your loved one’s device using a top-rated monitoring app. Alternatively, the solutions discussed above might come in handy if push comes to shove. We highly recommend Phonsee as the best app to tap into someone’s phone.

Jeremy White, a seasoned cybersecurity expert, delves deep into the labyrinth of social media vulnerabilities. With a wealth of knowledge and experience, he navigates the intricacies of digital landscapes, uncovering threats and fortifying defenses. Jeremy’s expertise shines in safeguarding against online risks, ensuring digital safety in an interconnected world.